CIA Triad Automation for Law Firms
Published on:
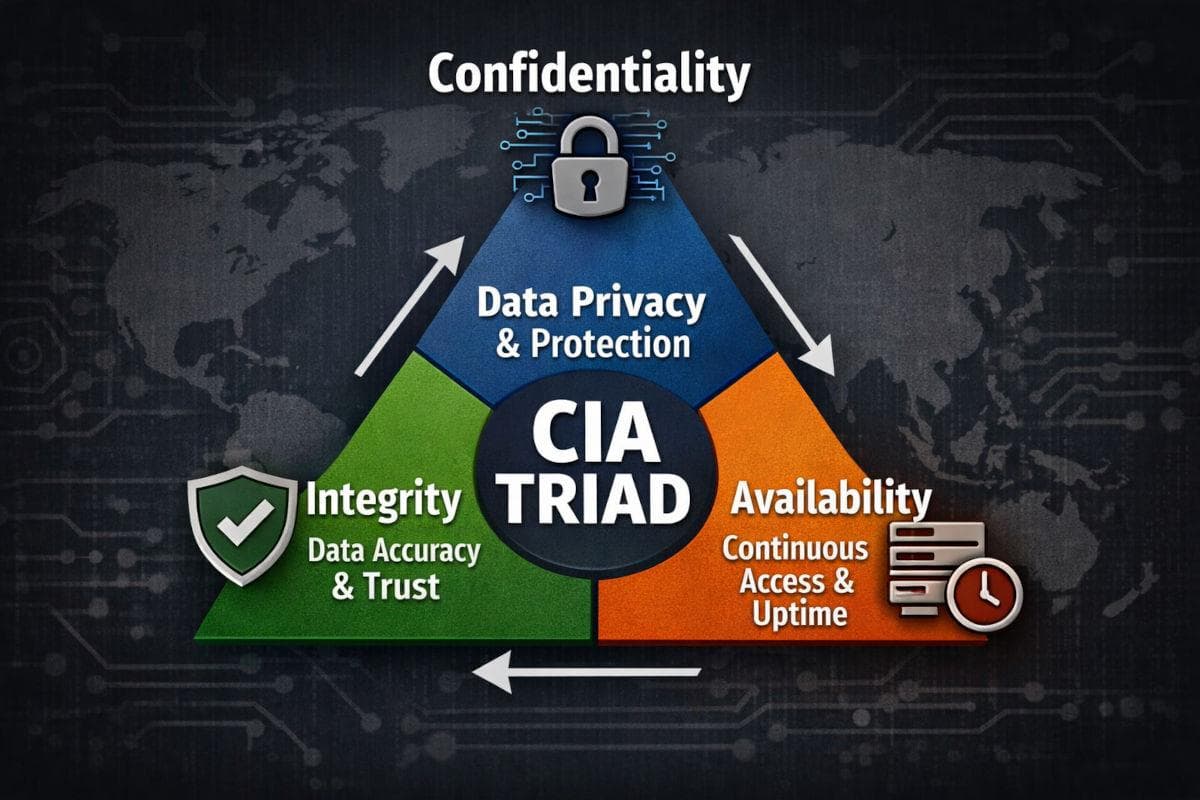
1 Why the CIA Triad is Important For Law Firms
Confidentiality, Integrity and Availability—three words every infosec auditor repeats. For sole practitioners and law firms, the stakes are higher: client privilege, chain-of-custody rules, regulator scrutiny. Yet most legal platforms tackle only one or two pillars and leave the rest to IT. Lexkeep was built to automate all three from the moment a file hits “Upload.”
This article maps each CIA pillar to concrete Lexkeep controls, then shows how it all plays out in real-world legal work.
2 Confidentiality—Keep Eyes Out
How Lexkeep Automates Confidentiality
• AES-256 at rest across EU cloud storage—no toggle, no extra fee.
• Encryption in transit for every connection.
• Optional end-to-end encryption (E2EE): files are cipher-text before they quit the laptop. Lexkeep never sees the key.
• Cohort permissions—Admin, Editor, Viewer—enforced by backend policy, not by “please remember to lock the folder.”
• Single sign-on and MFA for Business & Enterprise tiers.
Impact for Legal Teams
• Privileged docs stay invisible to cloud admins and platform staff.
• A lost laptop or phished password is a nuisance, not a breach.
3 Integrity—Prove Nothing Moved
How Lexkeep Automates Integrity
• File hash (its digital fingerprint) is computed automatically on upload.
• Blockchain anchoring on Ethereum—hash is written to an immutable block with its own timestamp.• Tamper-evident audit trail—every upload, share, legal hold and deletion request lands in a chained log.• One-click File Integrity Certificate—uploader, cohort, hash and block number in human-readable PDF.